Phala Joins The Linux Foundation and The Confidential Computing Consortium | by Phala Network | Phala Network | Medium

Applied Blockchain joins Confidential Computing Consortium to develop Applications in Energy&Banking

iExec RLC - Official | Hiring! on Twitter: "We are honored to announce that #iExec is now an official member of the Confidential Computing Consortium. The organization gathers major tech companies including
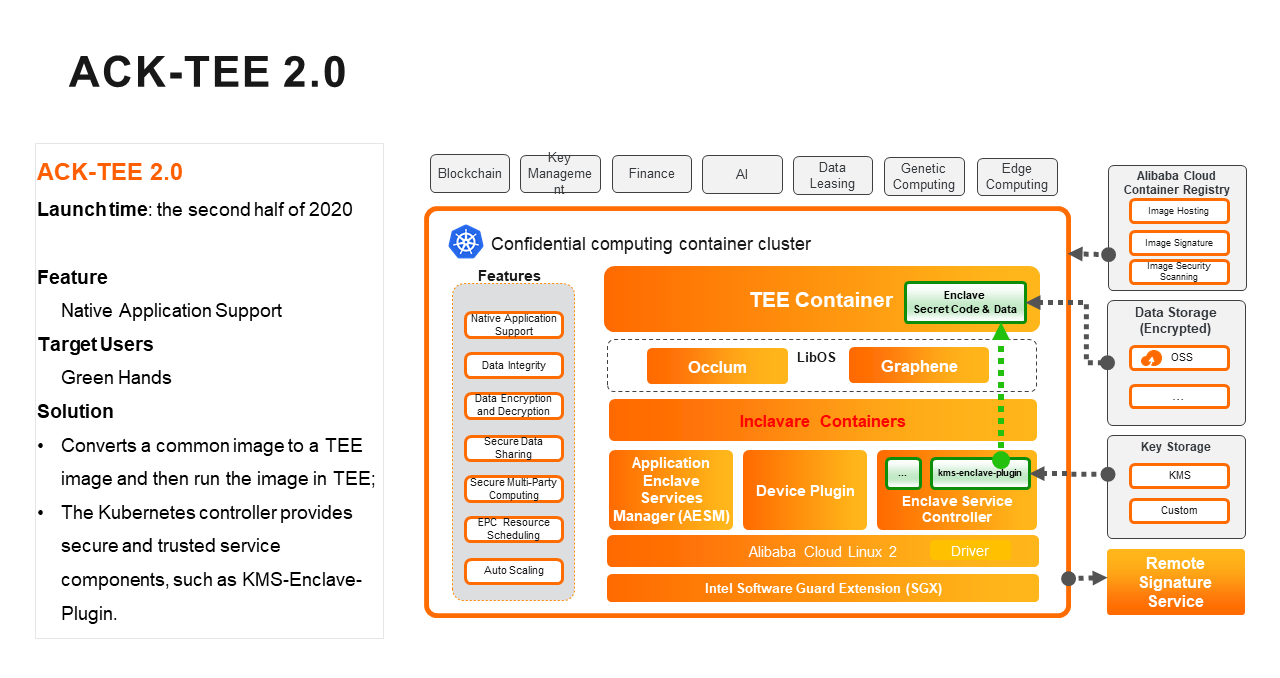
When Kubernetes Encounters Confidential Computing, How Does Alibaba Protect the Data in the Container? - Alibaba Cloud Community