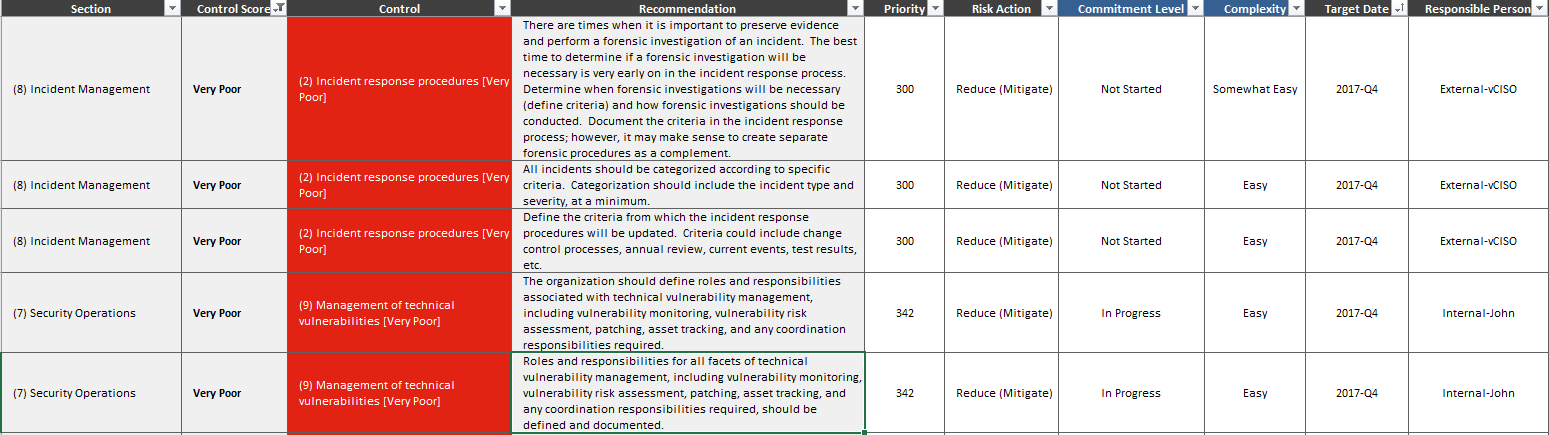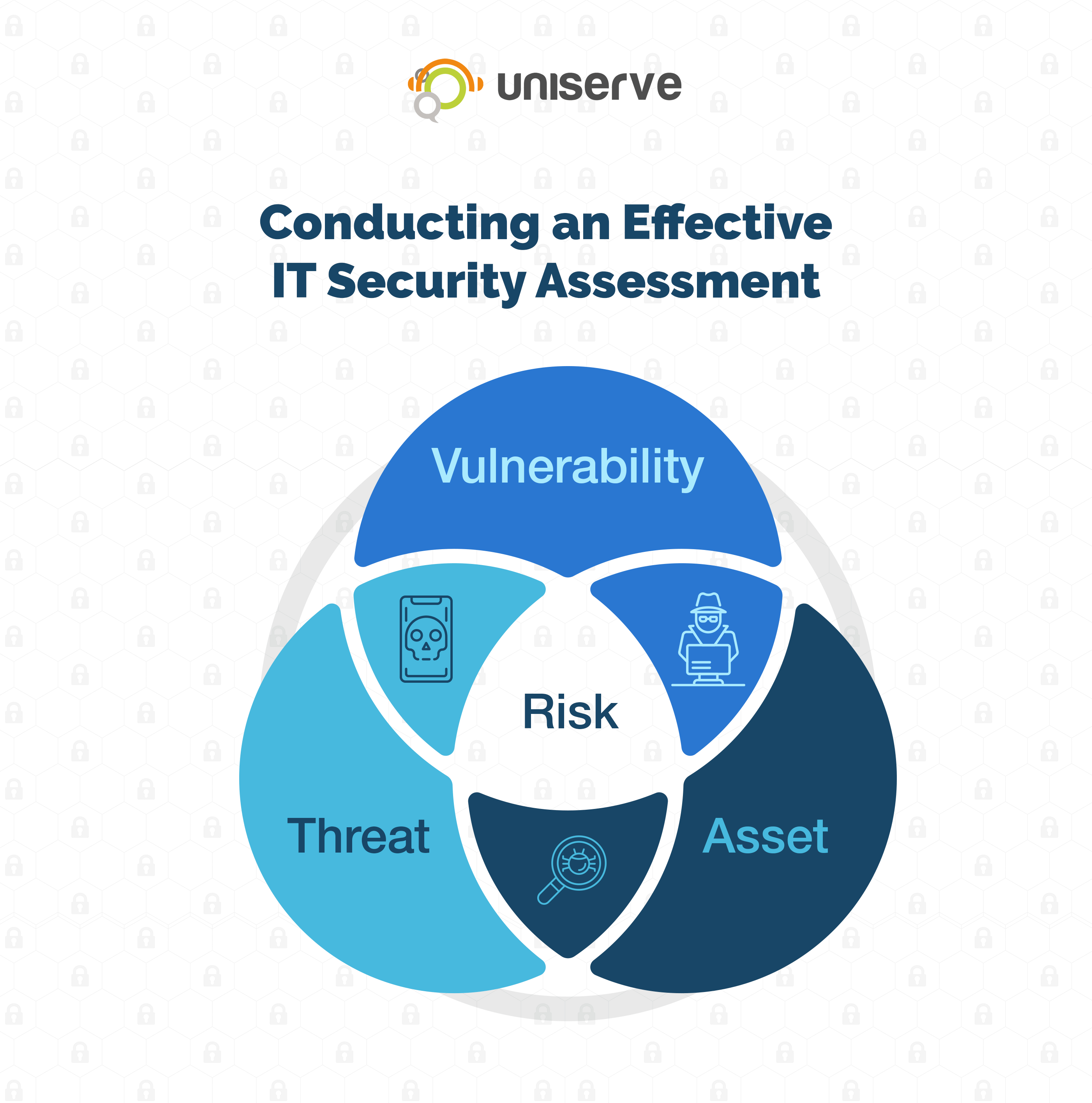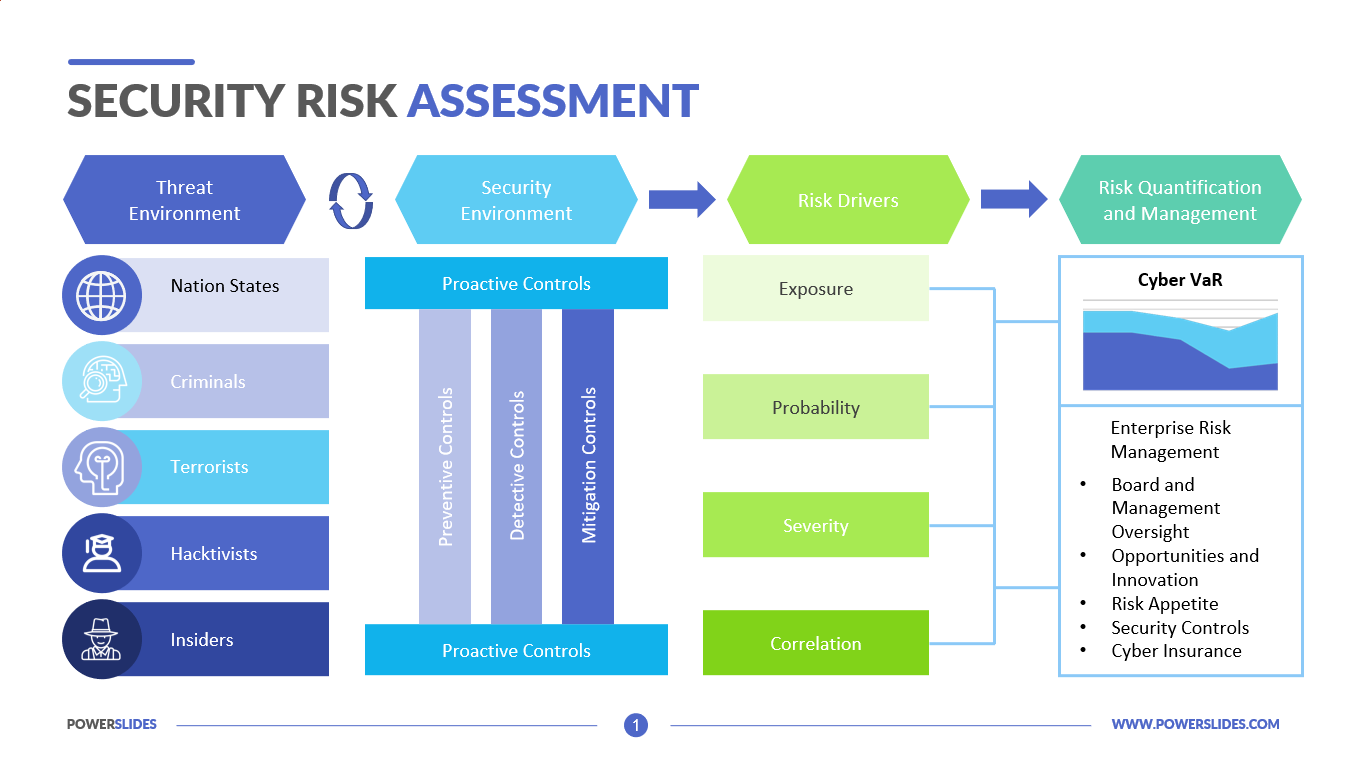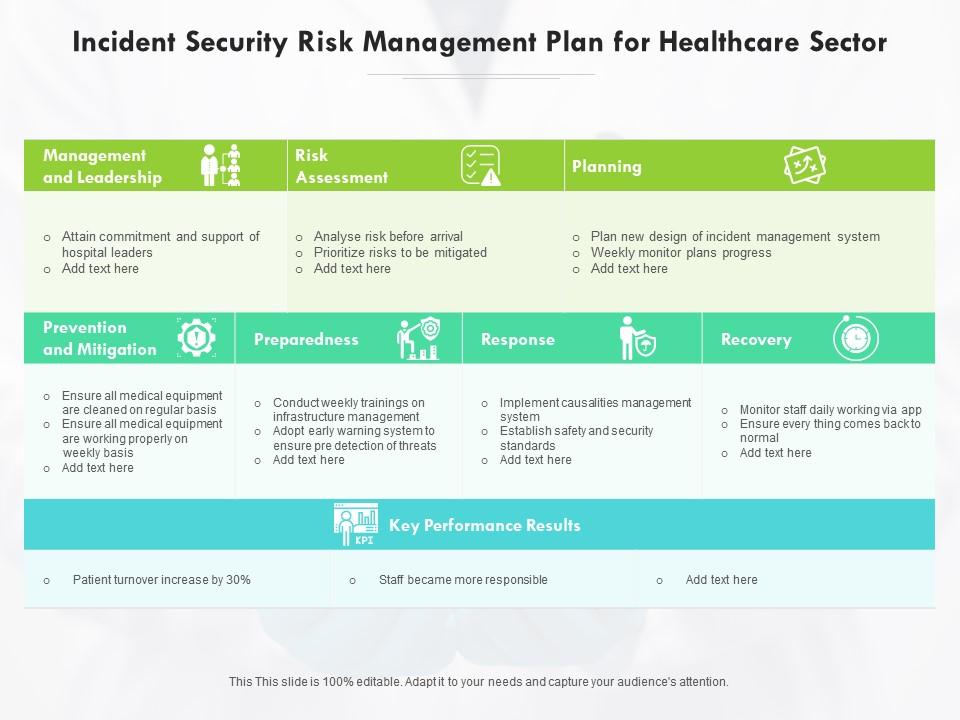
Incident Security Risk Management Plan For Healthcare Sector | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

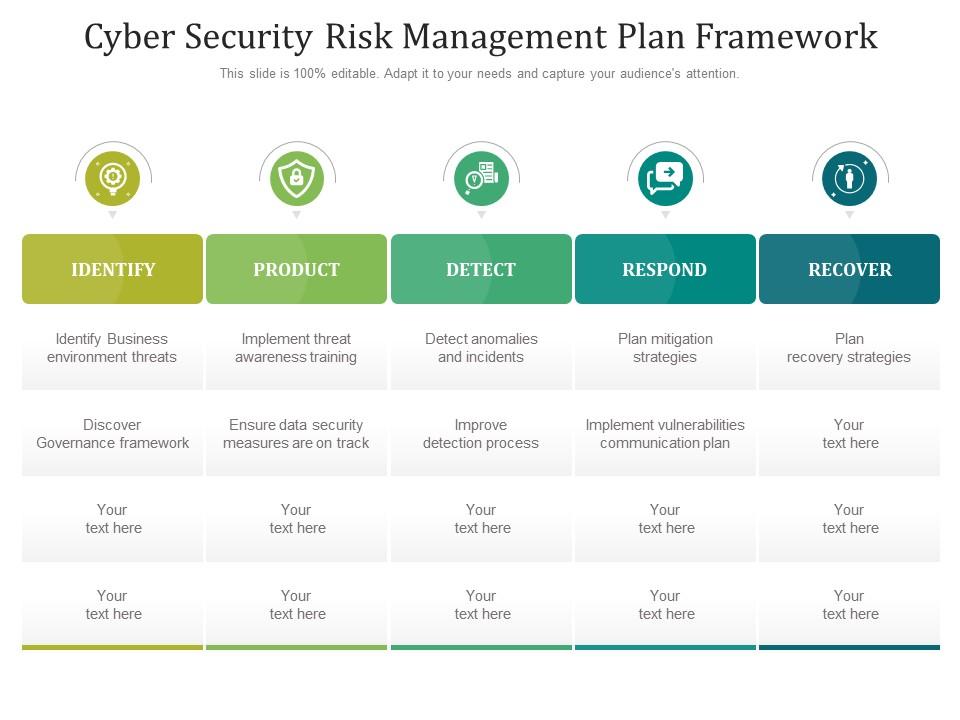
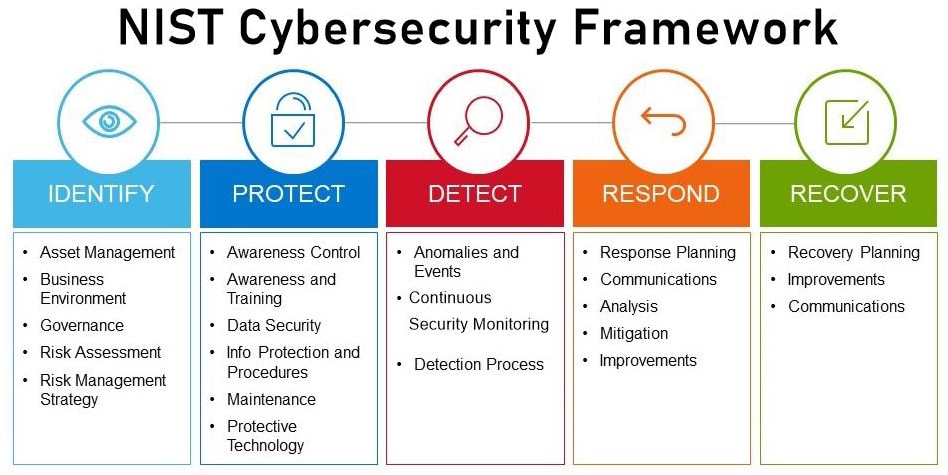
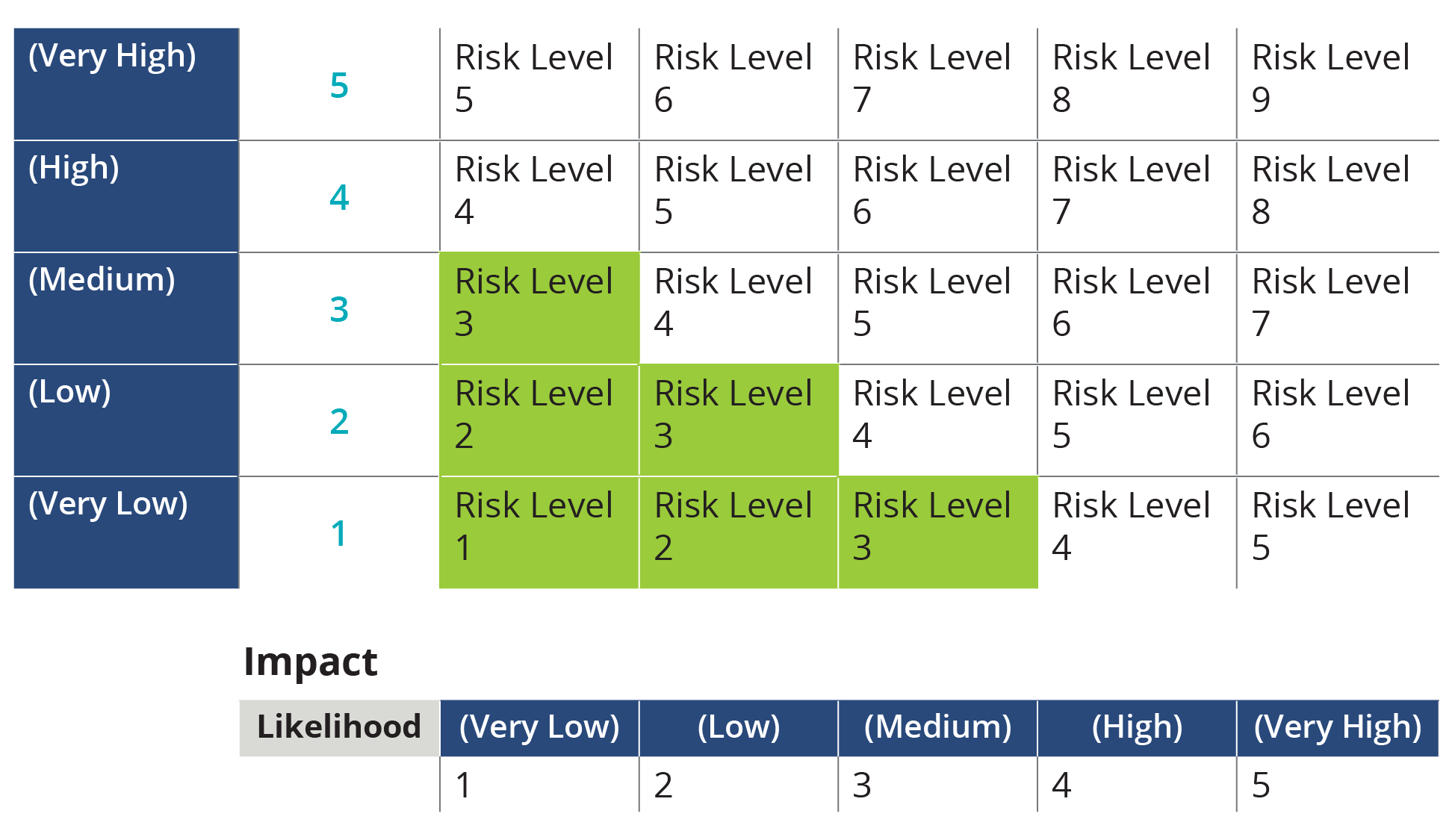
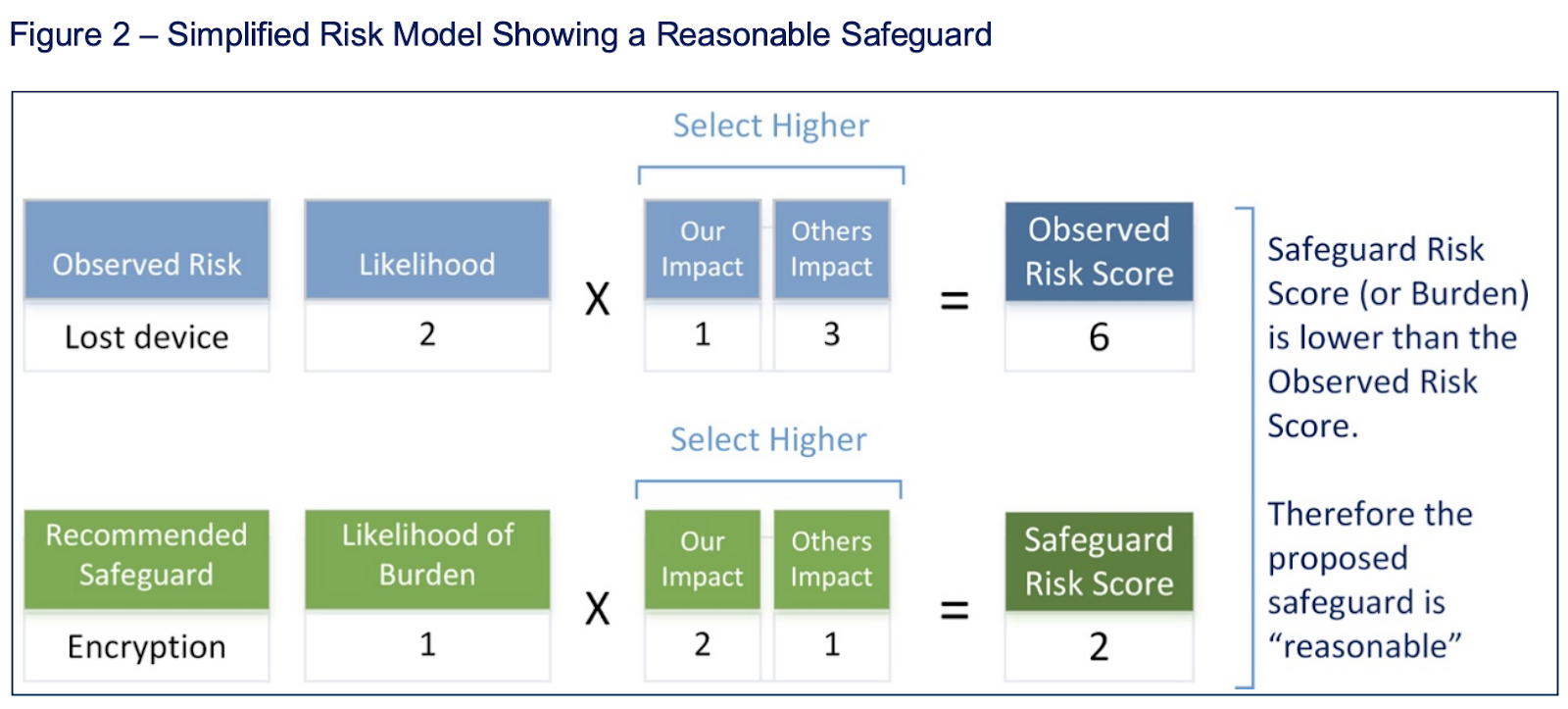
Cyber Security Risk Management Plan Information Security Risk Assessment Worksheet Consequences Diagrams PDF - PowerPoint Templates
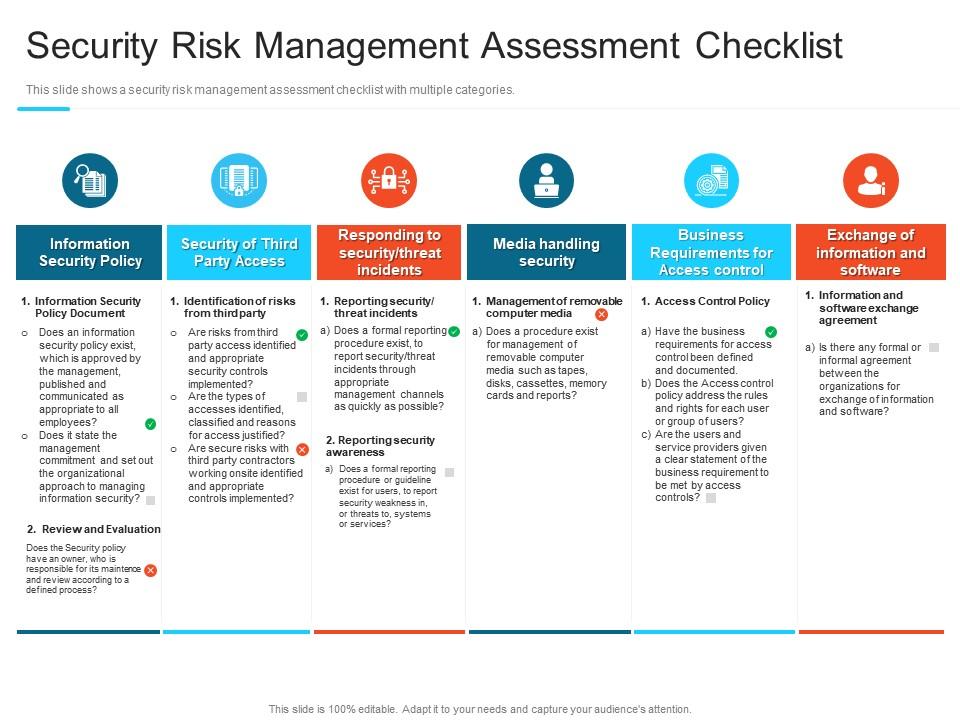
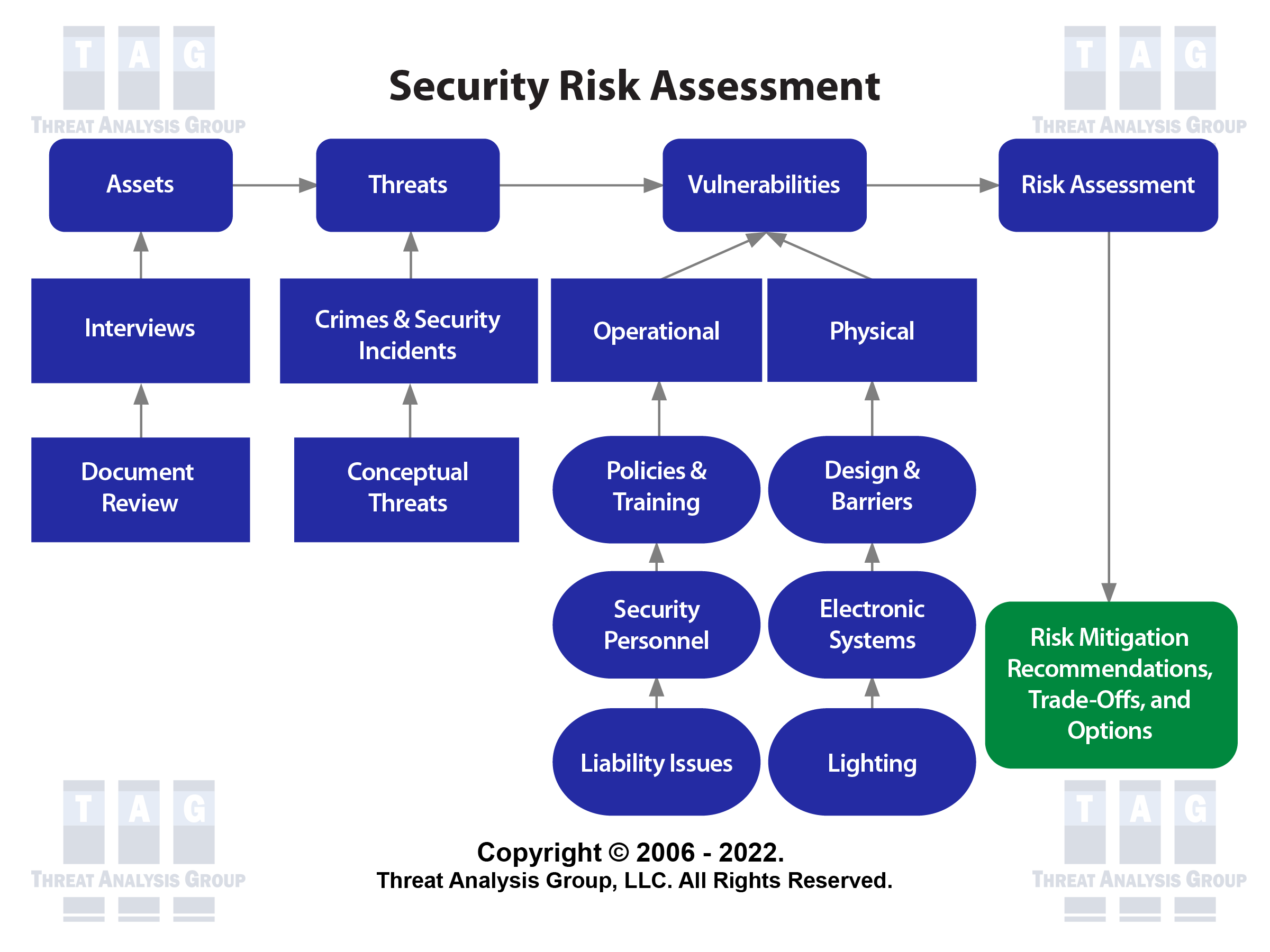
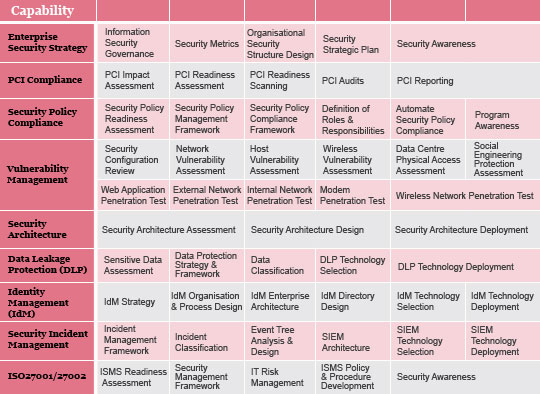
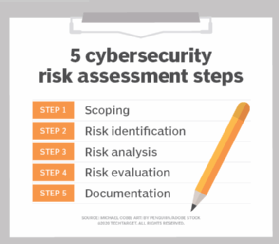
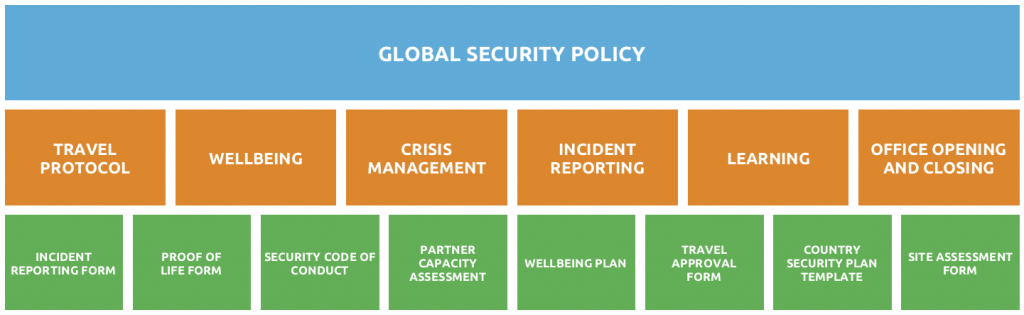
Security Risk Management Assessment Checklist Steps Set Up Advanced Security Management Plan | Presentation Graphics | Presentation PowerPoint Example | Slide Templates